The proliferation of edge devices in vehicles is accelerating due to growing consumer demand for new features such as such as lane drift warnings, cross traffic and blind spot alerts, gesture-based controls, child presence sensors, and automated "baby on board" modes.
Ensuring the security and functionality of the advanced edge devices that provide these features is increasingly challenging. Manufacturers must implement robust strategies to secure maintenance and updates to ensure reliable operation and protect against ever evolving threats. Strategies adopted in secure edge devices include Hardware Security Modules (HSM), cryptographic libraries, a zero-trust security model, and lightweight blockchain technologies for traceability and audits.
Importance of Maintaining Secure Edge Devices
Advancements in processor technology and PCB miniaturization enable automotive edge AI for predictive maintenance and improved performance. However, these compute-intensive systems require regular updates and maintenance for:
-
Security: Patch vulnerabilities to prevent unauthorized access and data breaches.
-
Performance: Optimize software and fix bugs to enhance device efficiency.
-
Compliance: Meet industry regulations by ensuring timely updates.
-
Longevity: Extend device lifespan by maintaining functionality and security.
Key Strategies for Secure Maintenance
Advanced Cryptography Algorithms
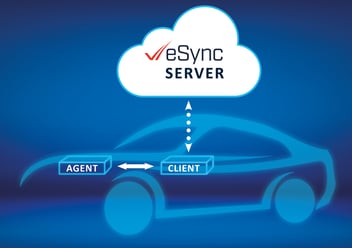
ECU suppliers are adopting modern cryptographic algorithms like Elliptic Curve Cryptography (ECC) and Post-Quantum Cryptography (PQC) to bolster ECU security. eSync's payload-agnostic capability enables delivery of cryptographic algorithms, allowing the eSync Agent for a particular secure edge device decrypt payloads for that edge device using proprietary methods, thus securing ECU communication programming.
Secure Boot
Secure boot ensures only authenticated and unmodified firmware runs on ECUs. Utilizing digital signatures (ECC or RSA) and hash functions (SHA-2 or SHA-3), eSync verifies firmware integrity and authenticity. Integration with blockchain establishes a chain of trust from a trusted root, ensuring secure boot processes.
Over-the-Air (OTA) Updates
eSync employs advanced cryptographic techniques for secure OTA updates, including AES encryption for data confidentiality, ECC/RSA for digital signature verification, and SHA-2/SHA-3 for data integrity checks during transmission and receipt. The Status Service of the eSync Client is pivotal in gathering and maintaining the state of edge devices to enforce OTA policies effectively. It can include memory integrity checks to assess memory availability, health, and quarantined memory status on each edge device.
The Status Service consolidates progress and status updates from all eSync Agents. This aggregated information is then accessible to the cloud orchestrator, facilitating real-time monitoring of OTA progress and device statuses.
All status information is timestamped to ensure accuracy, and the Status Service promptly updates its data upon command. This ensures the information remains timely and reliable, supporting informed decision-making and proactive management of OTA operations.
Regular Vulnerability Assessments
The eSync OTA Platform stands out for its comprehensive support of audit trails and versatile log extraction formats, crucial for maintaining the integrity and security of edge devices. These features ensure that a detailed record of all system activities is maintained, facilitating thorough analysis and accountability.
Regular security assessments are integral to the eSync OTA Platform's approach, blending automated scans with manual penetration testing to proactively pinpoint vulnerabilities. By identifying and mitigating potential risks early on, these assessments bolster the resilience of both edge devices and their firmware against emerging threats.
Moreover, these proactive measures not only strengthen security but also streamline the maintenance processes for edge devices. They provide valuable insights into the operational health and failure conditions of devices, enabling informed decisions on maintenance schedules and potential replacements. This proactive approach helps optimize device performance and reliability over their operational lifespan.
In essence, the eSync OTA Platform's combination of robust audit capabilities, rigorous security assessments, and insightful analytics ensures that edge devices operate securely and efficiently in dynamic automotive environments, safeguarding both data integrity and operational continuity.
Zero Trust Security Model
eSync's zero-trust approach requires continuous verification of device identity and integrity, strict access controls, and constant monitoring. All trusted sources must present certificates before secure communication channels are established, ensuring robust authentication and data protection.
Conclusion
Ensuring the security and functionality of edge devices in vehicles is paramount. Robust strategies encompassing OTA updates, advanced cryptography, blockchain integration, vulnerability assessments, and a zero-trust security model provide a comprehensive framework. These measures safeguard against threats, maintain operational reliability, and uphold data security, meeting the evolving demands of connected vehicle technologies.
FAQs
1. Why is edge device security critical in modern connected vehicles?
Edge device security is critical because vehicle features like ADAS, child presence detection, and predictive maintenance rely on compute-intensive ECUs processing real-time data. Without strong security controls, these edge devices become vulnerable to cyberattacks, data breaches, and unauthorized firmware changes, putting vehicle safety, compliance, and reliability at risk.
2. How does eSync secure OTA updates for automotive edge devices?
eSync secures OTA updates using layered cryptographic protection, including AES encryption for data confidentiality, ECC or RSA for digital signature verification, and SHA-2 or SHA-3 for integrity checks. Its Status Service continuously monitors device health, memory availability, and update progress, enabling secure, policy-driven OTA delivery across distributed automotive edge devices.
3. What role does secure boot play in protecting automotive ECUs?
Secure boot ensures that only authenticated and unaltered firmware can run on an ECU. By validating digital signatures and cryptographic hashes at startup, secure boot prevents malicious or unauthorized code execution. When combined with blockchain-based trust chains, it establishes a verified root of trust for automotive edge devices throughout their lifecycle.
4. How does a zero-trust security model improve edge device maintenance?
A zero-trust security model improves edge device maintenance by continuously verifying device identity, integrity, and access permissions before any communication or update occurs. This approach minimizes attack surfaces, enforces strict authentication, and ensures that only trusted devices and services can participate in OTA updates and diagnostics within connected vehicle ecosystems.

Leave a Comment